Certification Authority Authorization (CAA)
What is CAA?
A Certificate Authority Authorization (CAA) record allows domain owners to restrict issuance to specified Certificate Authorities (CAs). CAA records prevent CAs from issuing certificates under certain circumstances. Refer to RFC 6844 for further details.
How does Cloudflare evaluate CAA records?
CAA records are evaluate by a CA, not by Cloudflare.
Setting a CAA record to specify one or more particular CAs has no effect on which CA(s) Cloudflare will use to issue a Universal or Dedicated SSL certificate for your domain.
Why must I disable Universal SSL if my CAA records exclude Universal SSL issuance?
Since Universal SSL certificates are share between customers, your CAA records may prevent issuance of another customer’s Universal SSL. Therefore, Cloudflare must disable Universal SSL for your domain to ensure your CAA records do not affect another customer.
CAA records are automatically add for the Universal SSL CA providers comodoca.com, digicert.com, and letsencrypt.org if Cloudflare’s Universal SSL is enable for your domain.
If you do not require Universal SSL from Cloudflare, Disable Universal SSL in the Crypto app.
Disabling Universal SSL will leave your Cloudflare enable DNS records without SSL support unless you have uploaded acustom SSL certificate (requires Business or Enterprise plan).
What records are added to keep Universal SSL enabled?
The following DNS records are automatically set if you continue to use Cloudflare’s free Universal SSL certificates:
example.com. IN CAA 0 issue "comodoca.com" example.com. IN CAA 0 issue "digicert.com" example.com. IN CAA 0 issue "letsencrypt.org" example.com. IN CAA 0 issuewild "comodoca.com" example.com. IN CAA 0 issuewild "digicert.com" example.com. IN CAA 0 issuewild "letsencrypt.org"
Do not use the Only allow wildcards option for the root record (which returns only issuewild records) for any domain that will use Cloudflare’s Universal SSL.
Used alone, issuewild only permits wildcard issuance. Therefore, Cloudflare cannot add your root domain to the certificate unless you specify the Allow wildcards and specific hostnames option in the Tag dropdown:
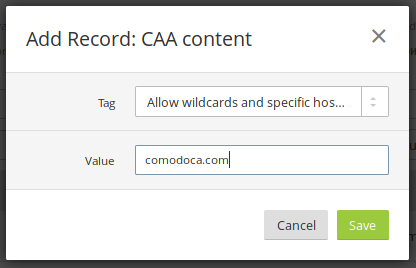
What happens when Universal SSL is disable?
Your domain name is immediately remove from the Universal SSL certificate and your users will observe SSL errors unless you upload a custom SSL certificate (requires Business or Enterprise plan).
How do I re-enable Universal SSL?
File a support ticket with Cloudflare Support.
What are the dangers of setting CAA records?
If you are part of a large organization or one where multiple parties are task with obtaining SSL certificates, include CAA records that allow issuance for all CAs applicable for your organization. Failure to do so can inadvertently block SSL issuance for other parts of your organization.

